Summary:
Aiming at the problem that the existing mobile ad hoc network security routing protocol can not take into account the data integrity and confidentiality, a secure routing protocol combining data integrity protection and data confidentiality protection is proposed. In terms of data integrity protection, a one-way hash function and key are used to generate a message authentication code to identify the integrity of the data in the routing; in terms of data confidentiality protection, the μTESLA protocol is used to transmit encrypted data packets, and different data packets are transmitted in different periods of time. The key, through the delayed disclosure of the symmetric key, simulates the asymmetric mechanism and reduces the resource consumption of authentication broadcast. Simulation experiments show that this method is not only better than existing routing protocols in terms of security, but also superior to existing routing protocols in terms of message delivery rate, routing overhead and end-to-end average delay evaluation indicators.
0 Preface
The Mobile Ad Hoc Network (MANET) is composed of many mobile devices that can communicate with each other. The nodes in the network can move freely to form a seamlessly connected self-organizing network that does not require the assistance of any basic communication facilities. It is widely used in military communications, disaster relief and environmental monitoring [1]. Because the nodes in the MANET network can move freely, the topology of the network often changes, and the communication link is at risk of interruption, which leads to an increase in packet loss. When the route is interrupted, it takes time to find the route again, which increases the end-to-end transmission delay and reduces the network throughput. At the same time, due to the limited power, memory, and storage capacity of the devices in the MANET network, all devices in the network need to share bandwidth, which requires energy loss to be considered during routing design. Therefore, optimal routing is the main challenge currently faced by mobile ad hoc networks [2-4].
At present, combined with the network characteristics of MANET, many meaningful routing protocols have been proposed, such as AODV[5-8], DSR[9-11], etc. These routing protocols combine performance indicators such as message delivery rate, end-to-end transmission delay, packet loss rate, network throughput, etc., to propose optimal routing strategies. In a multi-hop network, each node cannot complete the data transmission task independently, and the communication between multiple nodes is extremely vulnerable to attacks. Security has become one of the important issues to be solved urgently in the routing protocol of the mobile ad hoc network [12].
To enhance the security of routing protocols, many routing protocols encrypt and authenticate the data sent and received by each node. For example, the SEAD [13] routing protocol uses a one-way hash chain to identify the sequence number and other information in the routing table update message to verify the reliability of the message. Ariadne [14] adds digital signature technology to the DSR routing protocol, which can prevent various types of Denial of Service (DoS) attacks. ARAN [15] uses public key encryption and authentication of IP addresses on the basis of the AODV routing protocol to prevent routing from being copied. SAODV [16] also adds security measures to the AODV routing protocol to enhance the security of routing. Specifically, it uses digital signatures to identify the invariant parts of the message, and uses hash chains to protect the hop count information. However, existing secure routing protocols mainly focus on information authentication and ignore the confidentiality of data after routing discovery.
This paper proposes a secure routing protocol that takes into account data integrity and confidentiality. It uses message authentication code (MAC) and encryption key algorithms to authenticate source nodes, destination nodes and intermediate nodes, and uses μTESLA protocol [17] to protect data confidentiality. Using a one-way hash function to reduce bandwidth occupancy and computational complexity can prevent multiple network attacks on the premise of ensuring the basic performance requirements of routing, and improve the security performance of routing.
1 Security of ad hoc network routing protocol
The commonly used routing protocols in mobile ad hoc networks are AODV and DSR. Both of these protocols are on-demand routing protocols. The nodes in the network only exchange routing information when they are needed for communication. However, these protocols do not consider the security of communication, and do not protect information such as the position between nodes during the transmission process. All wireless devices within the communication range can obtain the content transmitted in the network, and are extremely vulnerable to impersonation and modification of data packets. Content and other attacks.
Attacks on routing protocols are mainly divided into two categories: active attacks and passive attacks. Passive attacks will only eavesdrop on the data transmitted on the network and will not disrupt the network. Active attacks will copy, modify, and delete data exchanged between nodes, reducing network performance or even destroying the network, and the impact is even worse. Classified according to the tools used in the attack, attacks can also be divided into external attacks and internal attacks. External attacks are typical active attacks that attempt to block the network, spread incorrect routing information, and even shut down the entire network. These attacks usually require security measures such as firewalls and encryption to prevent them. Internal attacks are mainly initiated by malicious nodes, and such attacks are more subtle [18-20]. Table 1 lists some commonly used attack types and preventive measures.
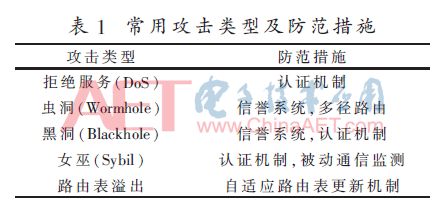
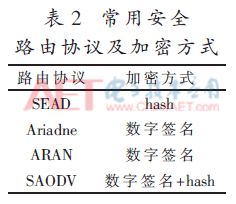
Encrypting and authenticating the data sent and received by each node is the main way to ensure communication security. Commonly used encryption methods are hash chain and digital signature. Table 2 lists the existing commonly used secure routing protocols and encryption methods.
2 A secure routing protocol that takes into account data integrity and confidentiality
This article assumes that the network connection in the wireless network is bidirectional, all nodes have synchronized clocks, and the interval key is used under loose clock synchronization. Encryption keys are generated and issued between nodes, so that every two nodes in the network share an encryption key. For example, the encryption key shared between the source node S and the target node D is KSD. This article uses μTESLA protocol to ensure the confidentiality of data, and information authentication uses message authentication codes and encryption keys.
2.1 μTESLA protocol
Generally, authentication broadcasting requires an asymmetric mechanism. However, the asymmetric cryptographic mechanism requires a large amount of calculations and consumes a lot of storage space, and is difficult to apply to devices with limited resources. The μTESLA protocol uses a delayed symmetric key to solve the above problems, which is an efficient broadcast authentication scheme. In the μTESLA protocol, each key in the key chain corresponds to a time period, and all data packets sent within this time period are authenticated by the same key. For example, suppose that data packets P1 and P2 are sent in time period 1, encrypted with key K1; P3 is sent in time period 2, encrypted with key K2. After receiving these data packets, first authenticate K1 through a one-way function K0=F(K1). If the authentication is successful, the receiving end uses the key K1 to decrypt the data packets P1 and P2. Similarly, in other periods, as long as the node receives the key Kj of the previous period, a set of one-way functions Ki=Fj-i(Kj) is used to authenticate the key Kj. If the authentication is successful, a new key Kj is authorized, which is used to decrypt all the data packets received between time periods i and j. Here, the one-way function uses the hash function.
In this strategy, the key disclosure is separated from the data packet broadcast and is only associated with the time period. The current key is broadcast periodically through a proprietary data packet.
2.2 Route authentication
Almost all routing attacks are caused by malicious intrusions or fake attacks to change routing data. In order to prevent these attacks, each node responsible for interpreting routing information must identify the originality and integrity of the data. This article combines the key and one-way hash function to generate a message authentication code, and authenticates each node in the route according to the message authentication code.
2.2.1 Route request
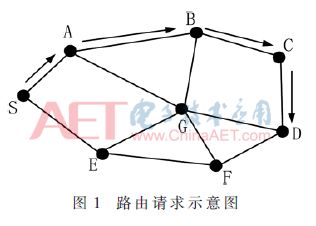
As shown in Figure 1, the source node S wants to establish a route between it and the destination node D, so that the source node starts route discovery towards the destination node and broadcasts a route discovery packet to its one-hop neighbor.

Each node repeats the above steps along the path, updates the data packet and forwards the broadcast to the destination node. In the data packet, (h0, h1,..., hn) contains the address and node serial number information used for intermediate node identification.
2.2.2 Route Response
After receiving the route request packet, the destination node sends a reply packet (REP) to the source node along the opposite path.
The first intermediate node receives the response data packet from the destination node D to the source node S:

Similarly, other intermediate nodes also attach their own MAC keys to the REP packet and forward them to the previous hop continuously. Finally, the form of the REP packet arriving at the source node is:
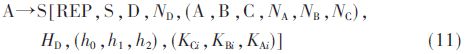
When the source node receives the routing response packet, it uses the MAC key and HD of the intermediate node to authenticate the message.
2.2.3 Route Maintenance
The topology of the self-organizing wireless network often changes, and the nodes in the network may increase or decrease, so that the routing may be interrupted. When the routing is interrupted, the routing error message (RERR) will be sent from the location where the error occurred to the source node, and then a new routing request will be initiated.
As shown in Figure 2, assuming that node C is out of the transmission range of node B, node B will generate a routing error message and send it to source node A through intermediate nodes B and A, in the following way:
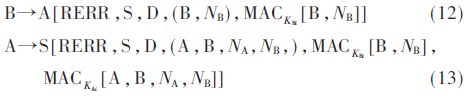
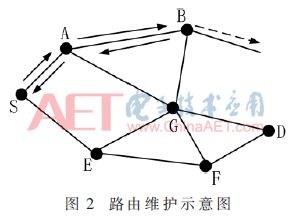
After the source node S receives the RERR message, it authenticates these MACs according to the MAC key of the intermediate node. After the authentication is successful, the source node requests route discovery again to find a new route.
2.2.4 Data confidentiality
Existing self-organizing network security routing protocols mainly focus on authentication, and rarely consider data confidentiality after routing discovery. This paper uses the one-way function in the μTESLA protocol to protect the confidentiality of data. In the routing phase, P is transmitted to the destination node through the routing request packet of the intermediate node, and decrypted by the encryption key of the source node and the intermediate node.
The initial key K0 of the one-way function is distributed among all nodes, and the destination node can use the one-way function to identify Ki, expressed as:

In this way, the receiving end can decode all the data packets sent in period i. When the time period i ends, the key Ki disappears and the source node sends a new key Ki+1. After the destination node receives the message containing the new key, it still uses the one-way function to authenticate the key Ki+1, and after the authentication succeeds, it uses it to decrypt all data packets sent in the i+1 period.
3 Simulation analysis
3.1 Simulation environment and evaluation indicators
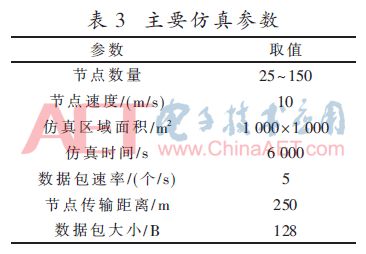
This article selects the internationally-used NS2 simulation platform [21] (the main simulation parameters are shown in Table 3), and compares the routing protocol of this article with the AODV[5], ARAN[15], and SAODV[16] routing protocols. From the aspect of anti-attack capability The performance of different protocols is compared qualitatively, and the performance of different protocols is quantitatively evaluated from the three aspects of message delivery rate, routing overhead and end-to-end average delay.
The quantitative evaluation index is [22]:
(1) Message delivery rate: the ratio of the data packets received by the destination node to the data packets actually sent;
(2) Routing cost: the ratio of routing packets to data packets;
(3) End-to-end average delay: the average of the time from the source node sending a message to the destination node receiving the message.
3.2 Security analysis
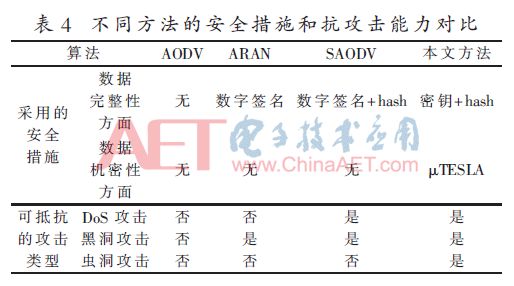
Table 4 compares the security measures and anti-attack capabilities of different methods. Among them, the AODV protocol does not use security measures, so it is difficult to resist various attacks; ARAN uses digital signatures for information authentication, which can resist black hole attacks; SAODV uses a combination of digital signatures and hash chains for information authentication, which can resist DOS and black hole attacks. In addition to using the key and the message authentication code generated by the one-way hash function for information authentication, the method in this paper also uses the μTESLA protocol to ensure the confidentiality of the data, which can resist the current mainstream DoS, black hole and wormhole attacks.
3.3 Performance evaluation
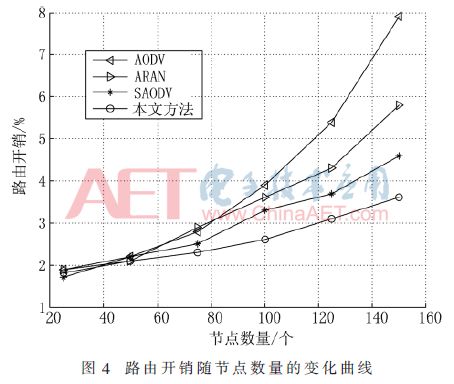
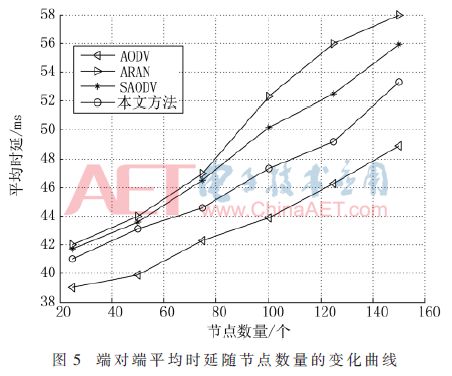
Figure 3 shows the comparison of the packet delivery rates of the four routing protocols under different numbers of nodes. Figure 4 shows the comparison of the routing overhead of the four routing protocols under different numbers of nodes. Figure 5 shows the comparison of the four routing protocols. Comparison of end-to-end average delays under different numbers of nodes.
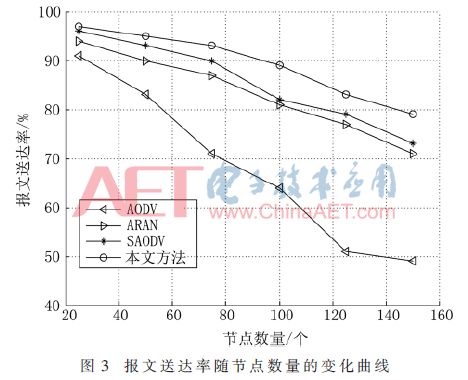
It can be seen from Figure 3 that the greater the number of nodes, the lower the message delivery rate. Compared with other methods, the message delivery rate of this method has the slowest decline, and when the number of nodes is the same, the message delivery rate of this method is higher than other methods.
It can be seen from Figure 4 that as the number of nodes increases, the routing overhead of the four methods also increases, but the growth rate of the method in this paper is slower, and when the number of nodes exceeds 50, the routing overhead of the method in this paper is the smallest.
It can be seen from Figure 5 that the end-to-end average delay will also increase as the number of nodes increases. The average delay of the method in this paper is lower than ARAN and SAODV two routing protocols that increase security measures. Although it is higher than the end-to-end average delay of AODV protocol, the security performance has been greatly improved.
4 Conclusion
This paper proposes a secure routing protocol based on MAC and μTESLA, which can solve the problem of data integrity and confidentiality in the existing secure routing protocols for mobile ad hoc networks. The method includes two parts: (1) Information authentication, the main measure is to use one-way hash function and key to generate message authentication code, and perform information authentication based on the message authentication code to protect the integrity of data; (2) Data confidentiality protection , Use the μTESLA protocol to transmit encrypted data packets. The protocol uses the delayed disclosure strategy of symmetric keys to implement asymmetric cryptography, which can effectively reduce the resource consumption of broadcast authentication. Through qualitative and quantitative comparison and analysis with the existing mainstream routing protocols such as AODV, ARAN and SAODV, it is confirmed that the method in this paper is not only more resistant to attacks than other routing protocols, but also message delivery rate, routing overhead and end-to-end delay, etc. The routing evaluation index is also better than other routing protocols.
Perfect fit: The Hydrogel Screen Protector is designed with a Soft TPU material, which can be completely covered even on a curved device, providing perfect protection for the full coverage of the screen.
Oleophobic and waterproof: The use of hydrophobic and oleophobic screen coatings can prevent sweat, grease residue and fingerprints without reducing screen sensitivity. It is almost invisible on the screen and brings a high-definition visual experience.
Sensitive touch: ultra-thin and Soft Hydrogel Film with a thickness of only 0.14mm. As time goes by, it will self-repair minor scratches, provide you with a highly responsive screen protector and maintain the original touch.
Easy to install: The installation of the Protective Film is very simple, without air bubbles. The protective sticker can stay on the phone perfectly, and the bubbles will disappear within 24 hours.
If you want to know more about Hydrogel Screen Protector products, please click the product details to view the parameters, models, pictures, prices and other information about Hydrogel Screen Protective Film.
Whether you are a group or an individual, we will try our best to provide you with accurate and comprehensive information about the Hydrogel Protective Film!
Hydrogel TPU Protective Film,Ultra-Thin Protective Film,Soft Hydrogel Film,Hydrogel Film Screen Protector,Screen Protective Film,Mobile Phone Screen Guards
Shenzhen Jianjiantong Technology Co., Ltd. , https://www.jjtphonesticker.com